
- Technology
- Advisory Services
- Advisory Services
- Training Programme
- Insights
- Company
- Contact Us
- Developers
- API Documentation
- ● Konsentus Verify
- ● Konsentus Certificate Chain Service
- Sandbox

Konsentus is wholly focused on the creation, implementation and management of trusted open finance ecosystems.
We provide specialist advisory services and central technology infrastructure to enable countries to set up and operate highly efficient safe and secure open finance ecosystems globally.
We are the only organisation providing end-to-end open finance advisory services combined with award-winning technology solutions to fast-track a country’s open finance implementation
in secure data exchange in open environments

customised to
market requirements

delivering interoperable multi-jurisdiction technology solutions

100% uptime
with zero outage
Advisory Services across
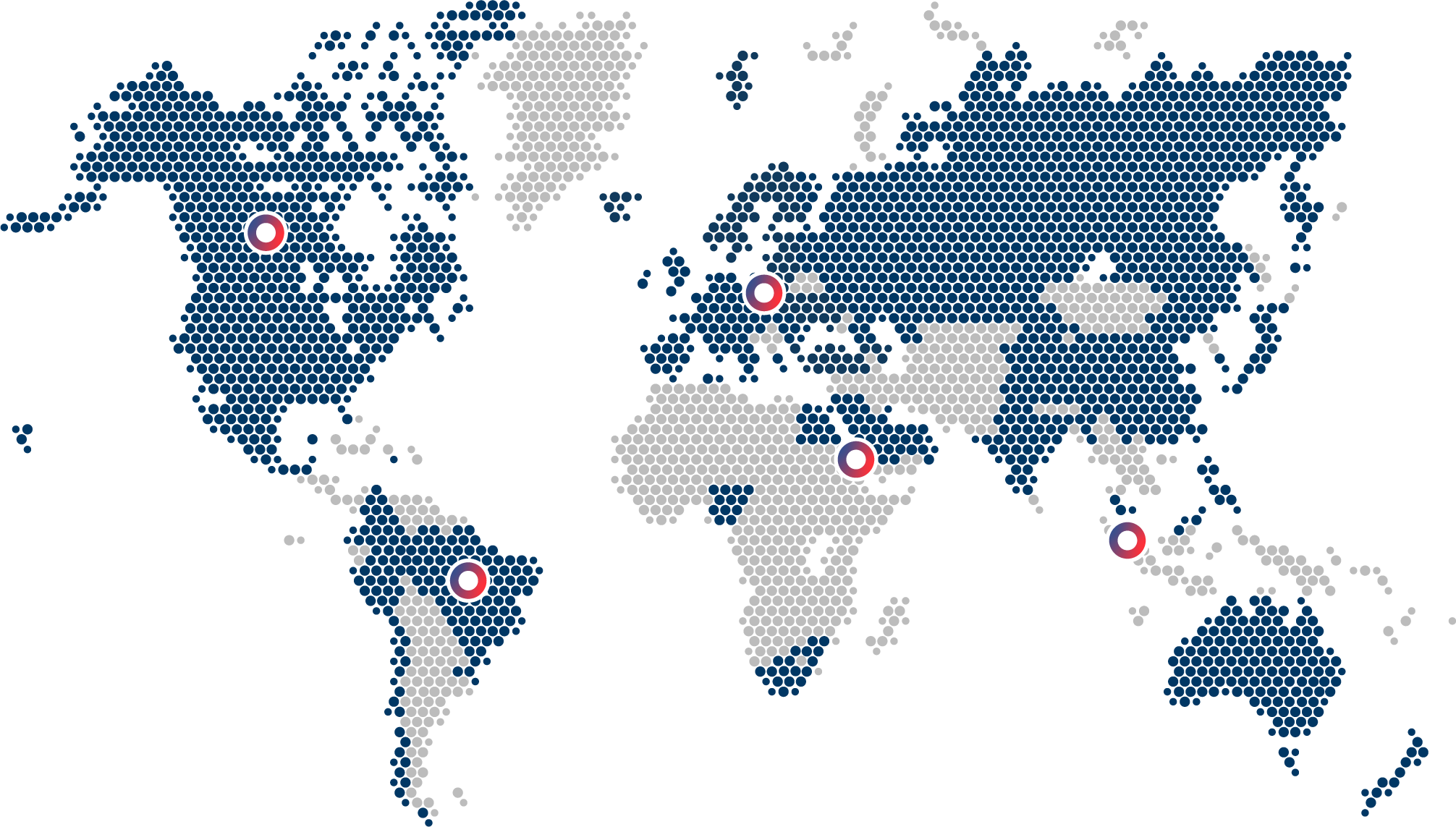
Active in
Consolidating data from
Our deep subject matter expertise across financial services and payments enables us to provide our customers and partners with technology solutions that are built for purpose and advisory services customised to local market requirements.

Accelerate the creation and operation of your protected open finance ecosystem.

Build, manage and maintain a secure open trust framework.

Seamlessly identify and interact with authorised participants of open finance ecosystems.
Remove the effort and complexity of onboarding third parties.



Regulators, central banks and industry partners across the globe consult Konsentus to help them define their open finance implementations and, our award-winning technology is trusted by over 250 financial institutions participating in open data frameworks.
Konsentus announces it has been selected by the Institute of Export & International Trade (IOE&IT) as one of three highly commended businesses in the Financial Services & FinTech category in the ‘Made in the UK, Sold to the World’ awards.
Join us at the FDX Spring Global Summit 2024, one of the most prominent events for the financial ecosystem in 2024.
Savis and Konsentus today announce that, together, they have created an operational structure for open banking in Vietnam.
Hanoi and London, 8 March 2024: SAVIS and Konsentus today announce that, together, they have created an operational structure for open banking in Vietnam.
In celebration of International Women’s Day 2024, Lauren Jones, our SVP Global Advisory, caught up with Shruti Awasthi, Global Open Banking & Innovation Leader.
Join Konsentus SVP Global Advisory, Lauren Jones at: Open Banking Excellence February Campfire: Open Banking Across Borders: Solving the Interoperability Challenge.
As the open banking and open finance market has started to mature, there has been a level of consolidation around key questions as part of any national programme.
This publication focuses on the regulatory-driven markets, all of which have approved competent authorities that authorise and supervise
Switzerland has a non-regulated open finance ecosystem. How is this supported in the market and what are organisations doing to ensure market adoption?
Singapore. 15 - 17 November 2023. This year's Singapore Fintech Festival showcased the intersection of Policy, Finance and Technology. Konsentus and our Partners Brankas showcased our strategies for central infrastructure and API ecosystems.
Konsentus' newly updated Open Banking and Open Finance World Map has found that there are now more than 65 national open banking programs globally.
Konsentus wins coveted Open Banking Pioneer, Organisation, at the prestigious Open Banking Expo Awards.

| Cookie | Duration | Description |
|---|---|---|
| _ga | 2 years | The _ga cookie, installed by Google Analytics, calculates visitor, session and campaign data and also keeps track of site usage for the site's analytics report. The cookie stores information anonymously and assigns a randomly generated number to recognize unique visitors. |
| _ga_TLMPP4GPZY | 2 years | This cookie is installed by Google Analytics. |
| _gat_UA-114071797-1 | 1 minute | A variation of the _gat cookie set by Google Analytics and Google Tag Manager to allow website owners to track visitor behaviour and measure site performance. The pattern element in the name contains the unique identity number of the account or website it relates to. |
| _gid | 1 day | Installed by Google Analytics, _gid cookie stores information on how visitors use a website, while also creating an analytics report of the website's performance. Some of the data that are collected include the number of visitors, their source, and the pages they visit anonymously. |

